Default behavior in Active Directory environment uses your domain controller with PDC emulator role as the primary source for time information and all other domain member servers and workstations use this time as authoritative.
To get the information about FSMO (Flexible single master operation) roles, type:
netdom query fsmo

If some of your domain controllers are virtualized, then your clock will soon be left behind. This happens because hyper-v host is obtaining time from primary source (virtualized domain controller) and after the clock on hyper-v host is set, then the same time will be set also on virtualized domain controller itself, creating a loop. During this loop, clock will shift bit by bit and left behind (a minute per week or so).
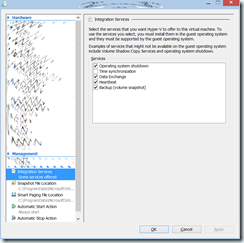
To overcome this situation, you need to disable hyper-v clock synchronization on all virtual domain controllers:
After that you should correct the time on PDC role owned domain controller. You should do this by using external time source. I suggest following commands:
w32tm /config /syncfromflags:manual /manualpeerlist:"ntp.data.ee"
w32tm /config /update
You can replace ntp.data.ee with some other time server on internet. To force the update you could use this command:
w32tm /resync
To show the configuration use this command:
w32tm /query /configuration
To reset messed up w32tm configuration, use following commands:
net stop w32time
w32tm /unregister
w32tm /register
net start w32time
This nice powershell script shows you time information on all domain servers:
$servers = Get-ADComputer -LDAPFilter "(operatingsystem=*server*)"
$servers | foreach {$server=$_.name ; net time \\$server} | clip
First line gets information about AD computers and selects only computers with server operating system. Second line uses net time command to get information for each server and places the result in clipboard, so you can paste it to excel, notepad etc.
Edit 27.04.2016 -------------------------------------------
Today, reconfiguring the situation, I found out, that the easiest thing to do is to use those 2 commands in PDC role owner:
w32tm /config /manualpeerlist:"pool.ntp.org" /syncfromflags:manual /reliable:yes /update
w32tm /resync
Edit 04.12.2018 --------------------------------------------
To see, which domain controller has wrong time in your environment:
$servers = Get-ADDomainController -Filter *
$servers | foreach {$server=$_.name ; net time \\$server | findstr Current}